Diffie-Hellman Encrypted Key Exchange
Diffie-Hellman Encrypted Key Exchange is often abbreviated to DH-EKE. It's one of the original EKE protocols based on Diffie-Hellman Key Exchange.
How It Work
Suppose we have two parties, Alice and Bob, want to build a secure communication via an established insecure channel. Eve is a attackers who is enable to eavesdrop all the messages on the channel.
Assume that Alice and Bob possess the same password , which is not leaked out and only they both know it. Therefore, this password can be used as a key for authentication. If we use this key to encrypt the data, only the one who knows the key can decrypt it. Some attackers without key are unable to pretend themselves as Alice or Bob. Nevertheless, the password is usually a human-memorable weak password. It will be easily cracked by performing an exhaustive search if its bits is too short. To make sure the shared key is long enough, we use the hash value of the password as the key instead. Thus, the shared secret key
Basic Concept
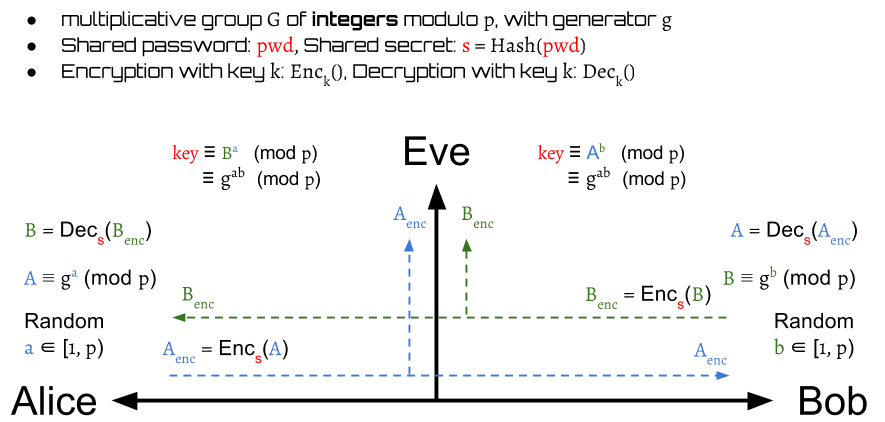
The basic idea is to use the shared secret key to protect the public key swap of Diffie-Hellman Key Exchange. Only the one who possess the key can encrypt and decrypt the public keys. They still can derive a symmetric session key $k$ on both sides for conversation.
With Challenge–Response Authentication
In fact, the DH-EKE is integrated by Diffie-Hellman and challenge–response authentication. The challenge is presented by one party, and another party must reply a correct answer to be authenticated.
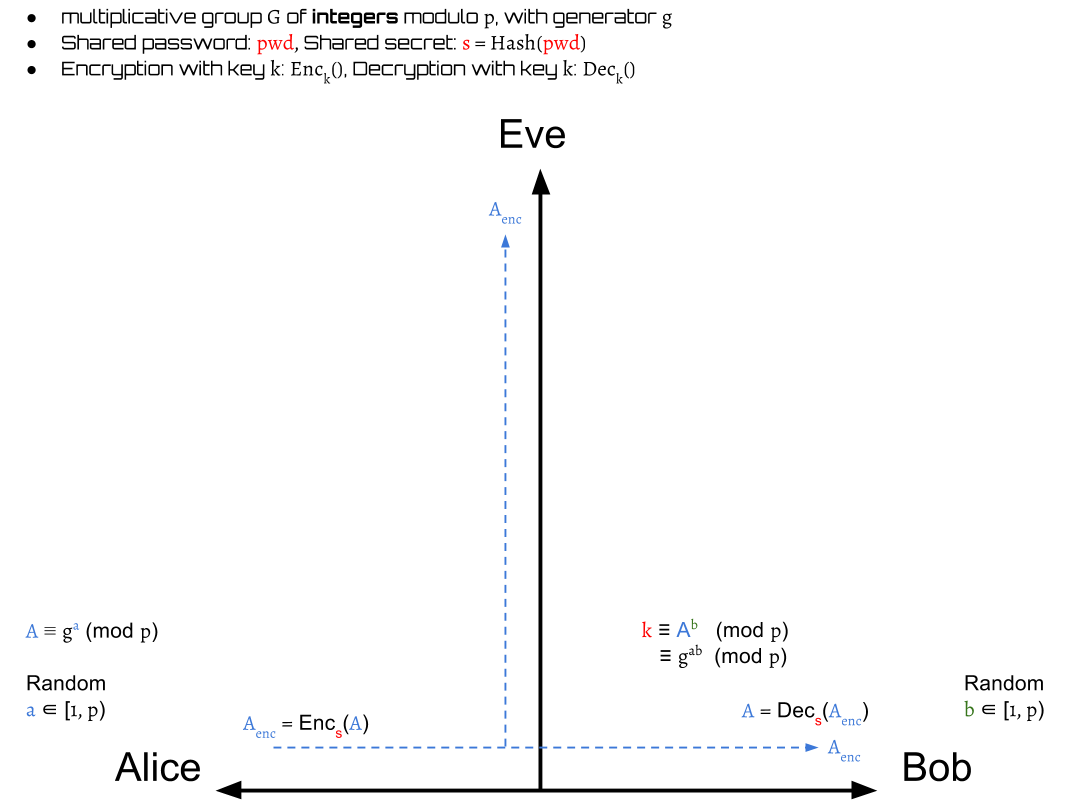
The first step of DH-EKE is very similar to DH. Alice picks a random number as her private key and use it to generate a public key: .
Then she sends the encrypted value of the public key: to Bob.
After receiving , Bob gets Alice's public key by decrypting .
Then Bob picks a random number as his private key to compute a session key: for encryption in this communication.
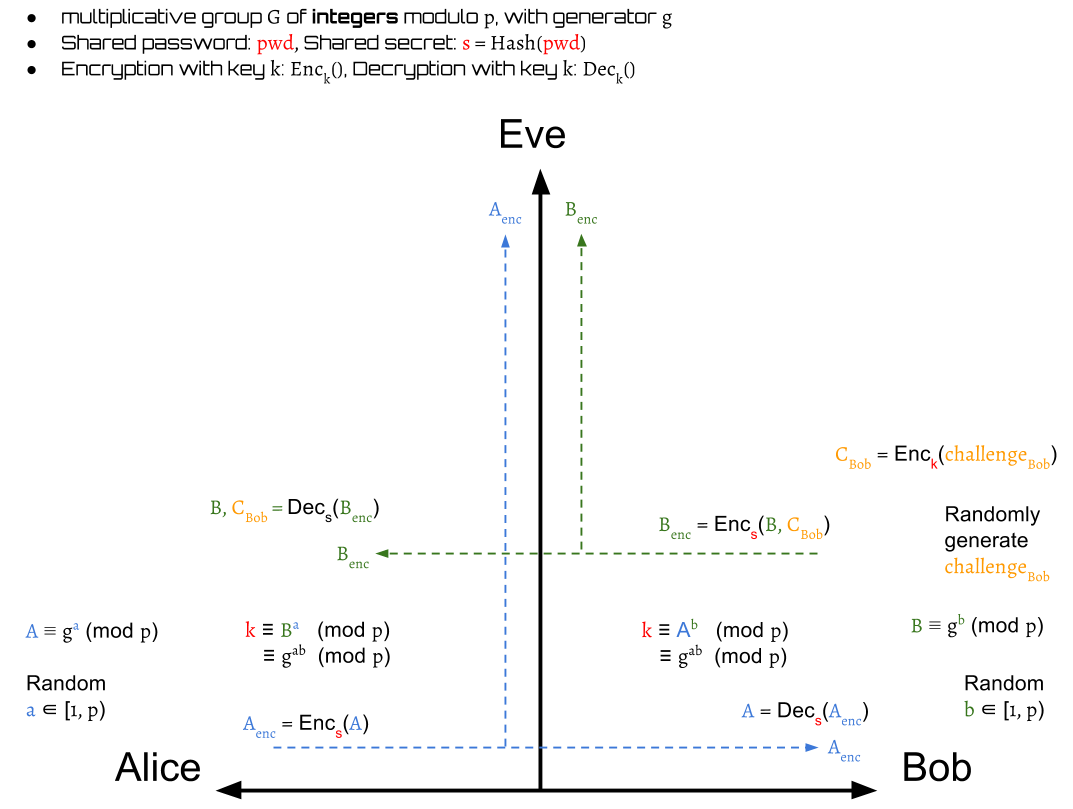
Next, Bob generates his public key and a random challenge . The is then encrypted by the session key into a value .
Then, Bob encrypts his public key with into by and sends it to Alice.
Alice decrypts the received to get Bob's public key and .
Then, Alice can compute a same session key as Bob by her own private key, .
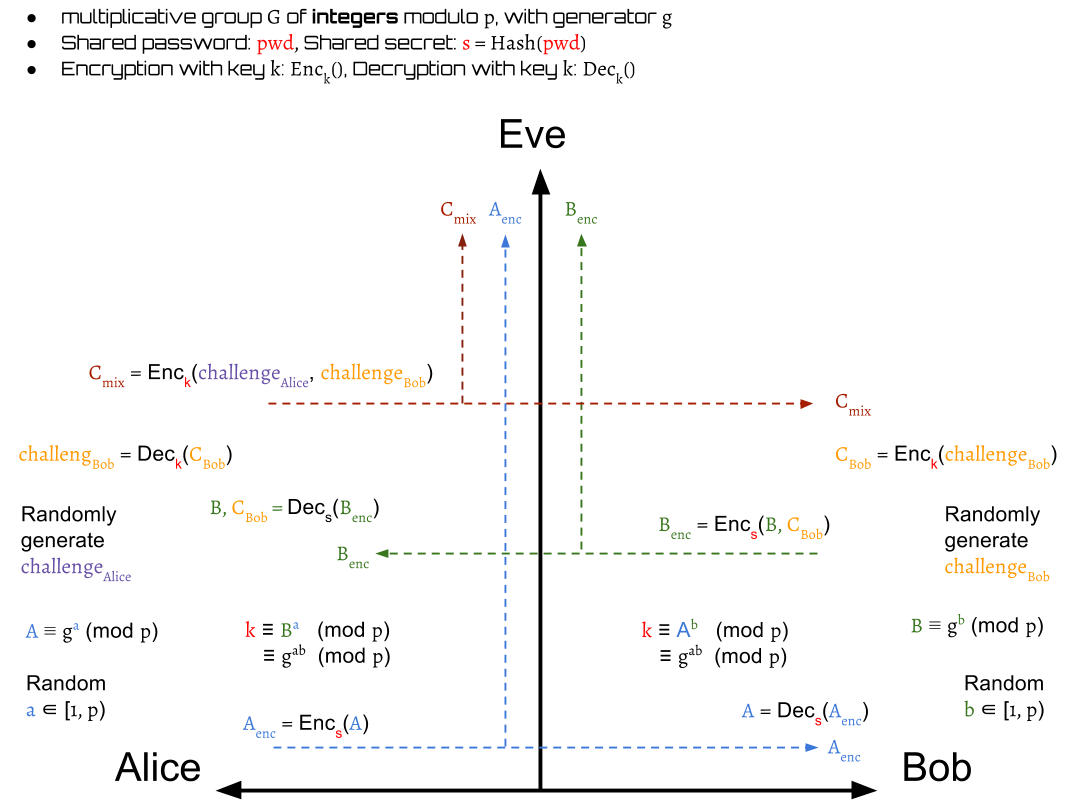
After Alice has , she can use it to decrypt to get . The here represents that Alice's decoded value of Bob's challenge.
Next, Alice randomly generates her own challenge and then use it to encrypt with Bob's challenge into a value by the session key
Then, Alice sends to Bob.

Later, Bob decrypts the to output and . The here represents that Bob's decoded value of Alice's challenge.
In this step, Bob can authenticate Alice is valid or not by checking her decoded value of his own challenge, .
If Alice is invalid, then Bob drops the session. Otherwise, Bob continue the protocols.
Next, Bob needs to prove his identification to Alice. He encrypts into and send it to Alice.
After receiving , Alice decrypts it to get Bob's decode value of her own challenge:
Alice now is also able to authenticate Bob:
Similarly, if Bob is invalid, then Alice drops the session. Otherwise, the protocol finishes.
Finally, Alice and Bob authenticate mutually and they both have a same session key that can be used for encryption or decryption.
Summary
- Alice generates a private-public key pair and
sends the encrypted public key to Bob
- Alice picks a random number as her private key
- Alice generates a public key
- Alice encrypts her public key by shared secret key
- Alice sends to Bob.
- Bob generates a private-public key pair and random challenge,
computes the symmetric session key by his private key,
and then sends the encrypted public key with the challenge to Alice
- Bob decrypts to get Alice's public key by shared secret key
- Bob picks a random number as his private key
- Bob computes a session key
- Bob generates a public key
- Bob randomly generates a
- Bob encrypts to by
- Bob sends to Alice.
- Alice get Bob's public key and challenge,
computes the symmetric session key by her private key,
then generates her random challenge
and send Bob's challenge back with her own one for authentication
- Alice decrypts the received to get by shared secret key
- Alice computes a session key
- Alice decrypts to get Bob's challenge by
- Alice randomly generates a
- Alice encrypts to by
- Alice sends to Bob
- Bob authenticates Alice by checking his own challenge with the received one
- Bob decrypts the received to get by
- Bob checks whether or not the received is same as his original one
- Alice is authenticated if the answer is yes. Otherwise, drops session.
- Bob encrypts the received to by
- Bob sends
- Alice authenticates Bob by checking his own challenge with the received one
- Alice decrypts the received to get by
- Alice checks whether or not received is same as her original one
- Bob is authenticated if the answer is yes. Otherwise, drops session.
Security Issues
Short Exponents
The packets are transmitted byte-by-byte, so its size of bits must be 8's multiple(1 byte = 8-bits). Thus, if the modulo is bits, then the group must bits. The private key, the public key are all bits.
Therefore, if , where , then some of bits are predictable. They must be 0. For example, if , then we know the range of the group is and the data is 2-bytes. The first 7 bits in the first byte are all 0 because the elements in the group are smaller than .
References
Encrypted Key Exchange: Password-based Protocols Secure Against Dictionary Attacks