Diffie-Hellman Key Exchange
Make two parties share secret messages.
Problem
How do you shared secret messages with someone who don't have a shared key? If they have the secret shared key, then they can use key crypto to encrypt/decrypt messages. Is it possible to build a secret shared key between two parties if they already have a insecure channel?
Alice, Bob, and Eve
Assume that there are Alice, Bob, and Eve. Alice and Bob want to talk to each other privately, but Eve can eavesdrop this channel. The problem is: Can Alice and Bob build a secure channel between them?
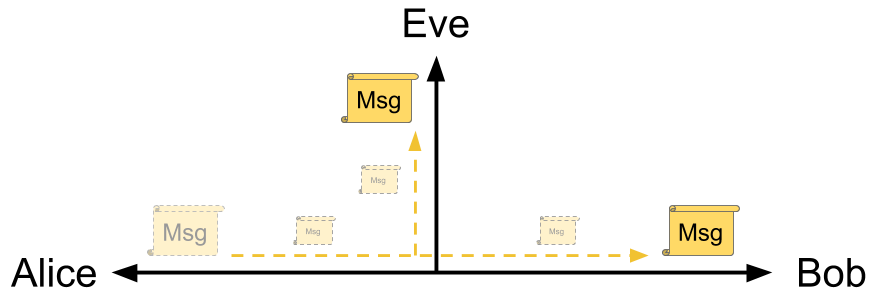
Passive Attacker: Eve, a eavesdropper
Eve can see all messages on the channel, but she can't modify them.
Concept: Diffie-Hellman in colors
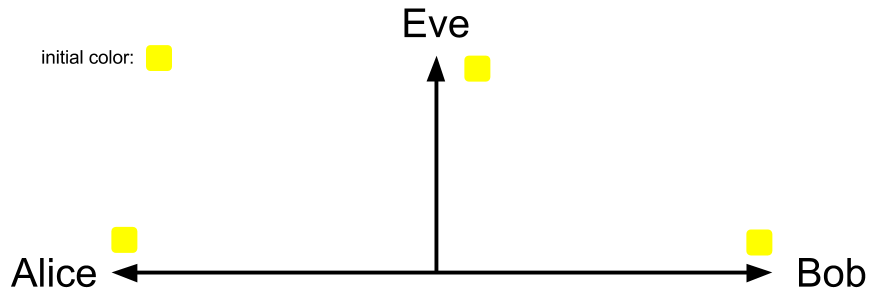
It's better to use the color-mixing to explain the Diffie-Hellman. At first, Alice and Bob agree to use a color Yellow as their initial color. This is not secret, so Eve can also know they will use yellow as their initial color.
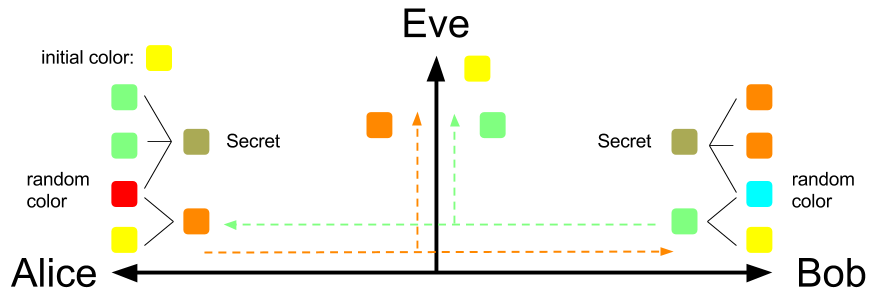
Next, Alice and Bob will randomly choose a secret color that won't tell anyone as their private key. Suppose Alice and Bob choose Red and Cyan respectively, then they will use their own secret color to mix with the initial color Yellow. After mixing the secret color with the initial color, Alice will get color Dark-Orange, and Bob will get color Light-Green as their public key.
Next, Alice and Bob will give each other their mixing color. Eve can eavesdrop the conversation between Alice and Bob, so she can know their mixing color too.
After Alice receives Bob's mixing color: Light-Green, she can make two copies of it and mixing these two with her own secret color: Red to get a final mixing color.
Similarly, Bob can produce a final color by mixing his own secret color with the two copies of received mixing color from Alice.
Surprisingly, Alice and Bob will generate the exactly same final color by the above step! They will both get Olive Green! The final color is the shared secret key between the Alice and Bob.
After they both generate the same shared secret key, they can use it to encrypt or decrypt their messages.
Summary
At first, Alice and Bob choose their own secret color:
- Alice: Red
- Bob: Cyan
Then they mix their secret color with the initial color:
- Alice: Yellow + Red = Dark-Orange
- Bob: Yellow + Cyan = Light-Green
Next, they give each other their mixing color, and then they both use the received mixing color to produce the final color:
- Alice: Red + Light-Green + Light-Green = Olive Green
- Bob: Cyan + Dark-Orange + Dark-Orange = Olive Green
Can we choose other colors?
This game works even Alice and Bob choose other secret colors. Why not try your own to test and see the results?
Try you own
You can play this game on online color mixing tool, like TryColors. If you want to re-produce our example, the used colors are:
| color | code |
|---|---|
| Yellow | #FFFF00 |
| Red | #FF0000 |
| Cyan | #00FFFF |
| Dark-Orange | #FF8000 |
| Light-Green | #80FF80 |
| Olive Green | #AAAA55 |
You can play our example online here. We already put all colors on it.
For those who is curious about the information of the produced colors, you can just enter the color code here to get the color's name.
Can Eve produce the final color?
Actually, Eve can produce the final color in this example if Eve know how Alice and Bob will mix those colors. However, if Alice and Bob finish their private conversation by using the shared secret key to encrypt/decrypt messages before Eve cracks the shared secret key, then the conversation can still be safe.
In real world, the shared key is not easy to crack as our example here. This will be well-explained after introducing the standard Diffie-Hellman below.
Diffie-Hellman in Math
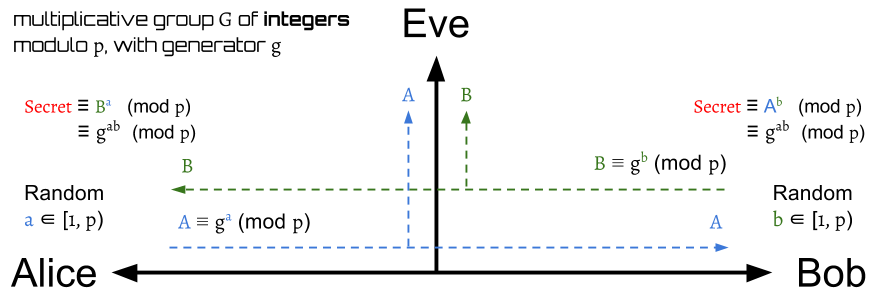
The initial setting between Alice and Bob from the original implementation of the protocol is a multiplicative group of integers modulo with generator , where is prime, and is a primitive root modulo p.
The protocol is pretty simple. First, both Alice and Bob agree to use one set of . Then, just like the color example, Alice and Bob will respectively choose a random integer , where ,as their private key.
Next, Alice and Bob will compute their public key , :
and send them to each other. That is, Alice will receive , and Bob will receive .
After exchanging the public key, Alice and Bob can use the received number to produce a shared secret key.
Let the shared secret key of Alice and Bob are and , and they are defined by:
(For those who are not familiar with the above operations, please read modular arithmetic in the appendix first.)
Thus,
Surprisingly, again, Alice and Bob will generate the exactly same shared secret key. They can use this key to encrypt the sent messages or decrypt the received messages.
Notice that are all located in range because the operation .
Examples
Let with prime and generator . It's easy to check the group by:
The indeed can generate all elements and the generated element will go back to the first at the times.
After checking our settings, we start to play the Diffie-Hellman. Suppose Alice picks and Bob picks , then
Next, Alice will send to Bob, and Bob will send to Alice. Then Alice and Bob can compute the shared secret key after receiving the other's public key.
It's obvious that is a symmetric key pair, so Alice and Bob can apply some symmetric key cryptography algorithm such as AES, DES, to encrypt and decrypt their messages.
The following table shows what Alice, Bob, and Eve know about the numbers for producing the shared secret key:
| Step | Alice | Eve | Bob |
|---|---|---|---|
| 0 | g = 2, p = 5 | g = 2, p = 5 | g = 2, p = 5 |
| 1 | a = 3 | b = 2 | |
| 2 | A = 3 | A = 3, B = 4 | B = 4 |
| 3 | SecretA = 4 | SecretB = 4 |
To get familiar with the Diffie-Hellman protocol, you can use the example groups in appendix to play it.
One Round-Trip Implementation
The whole Diffie-Hellman can be actually done in one round-trip communication:
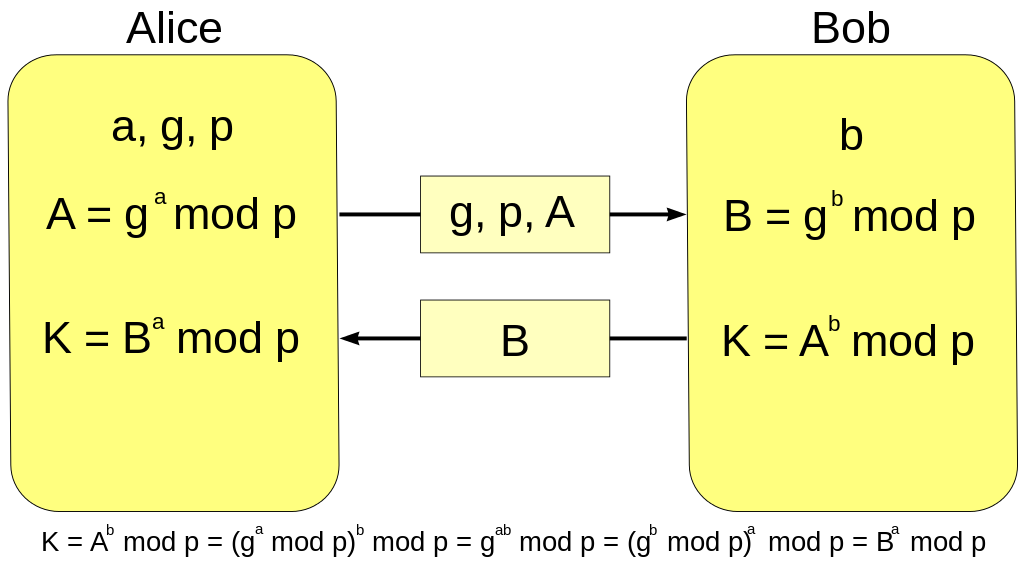
Can Eve compute the shared secret key?
The answer depends on whether and are chosen properly. In particular, the bigger of the size(or the order) of the group is, the better the security between Alice and Bob is.
When the size of is small, like the above example, it's easy to crack the secret key from the public key.
For instance, Eve can list all power-value pairs upon she knows and . The power and value is actually the secret key and the public key.
| power(secret key) | value(public key) |
|---|---|
| 1 | 2 |
| 2 | 4 |
| 3 | 3 |
| 4 | 1 |
With the above table, she can easily get the correct secret keys after receiving the public keys. When Eve receives , she can look up the table to find the .
However, if the size of group is very large, then it will be very hard to list all the numbers and search the matched secret keys. This is actually the base of our network security today. The function is one of the trapdoor functions, or one-way function functions. It's easy to use to compute , yet difficult to find its inverse function to get . The inverse function here is called discrete logarithm problem. It is considered to be computationally intractable. Currently there is no efficient algorithm to compute the discrete logarithms in general.
Thus, when is a very large number(the size of will be very large), then Eve is currently impossible to eavesdrop the messages between Alice and Bob.
(See more of trapdoor function here.)
Generalization to Finite Cyclic Groups
Diffie-Hellman protocol is actually can be generalize to finite cyclic groups, instead of specifying with the multiplicative group of integers modulo . In practice, Elliptic Curve Diffie–Hellman protocol is usually a better choice. It can achieve same security with less computation.
- Alice and Bob agree to use a finite cyclic group of order and a generator . The operation is defined: , where is the operator of the group.
- Alice randomly picks a number , , and send to Bob.
- Similarly, Bob picks a random number , , and send to Alice.
- Alice computes
- Bob computes
The must be a one-way function and there should be no efficient algorithm to compute given and , otherwise, the communication is insecure.
General Model
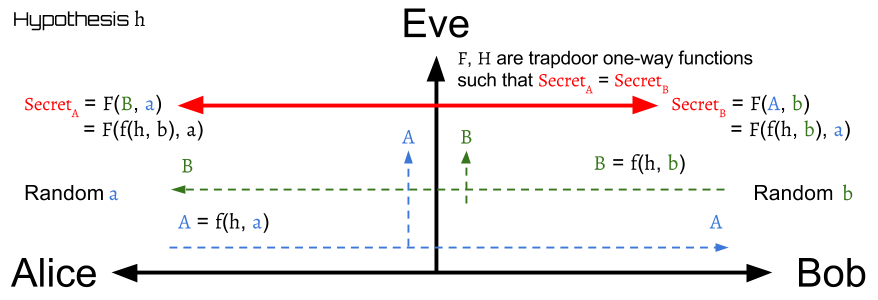
From the above two examples of Diffie-Hellman, we can find its general model. The general model is shown on above figure.
To make sure the communication is secure, function must be one-way function and there must be no efficient method to compute the given .
The standard DH implementation
We demostrate the original implementation of Diffie-Hellman in the general model below.
The Hypothesis and the Function Operation
Hypothesis is the group geneator , and the function are defined:
Alice
Alice first randomly choose a secret number , , where is the order of the group. Next, Alice will compute a public key and send it to Bob. Then Alice will receive Bob's public key and then use it with secret number to derive the shared key . (For those who are not familiar with the following operations, please read modular arithmetic in the appendix first.)
Bob
Similarly, Bob first randomly choose a secret number , , where is the order of the group. Next, Bob will compute a public key and send it to Alice. Then Bob will receive Alice's public key and then use it with secret number to derive the shared key .
For Color Calculation
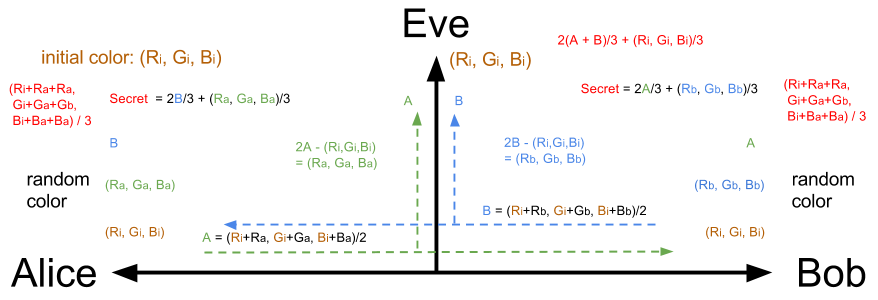
Color Code
All of the color are mixed by red, green and blue lights. They all can be coded in a RGB set , where is for red light, is for green light, is for blue light.
Operations
The operations of color code are defined:
- , where is a constant.
- , where can be any operator like .
Color Mixing
Suppose we have n colors: , where . The mixing color for these n one is
The Hypothesis and the Function Operation
Hypothesis is the group geneator , and the function are defined:
Alice
Randomly choose a secret color .
The mixing color , , will be sent to Bob, and Alice will receive a mixing color from Bob. Then can be derived by and .
Bob
Randomly choose a secret color
The mixing color , , will be sent to Alice, and Bob will receive a mixing color from Alice. Then can be derived by and .
Real World Usage
The symmetric secret key is almost never used as the cryptographic key directly since it may have some weak bits. One possible solution is to use its hash value instead to overcome this weakness.
Weak of DH: No Authentication

Diffie-Hellman protocol has an obvious weak: It has no authentication mechanism. Neither side of the exchange is authenticated. Alice and Bob indeed can generate a shared secret key, but Alice can't distinguish whether or not Bob is the real one, and Bob can't know whether or not the one he is talking to is Alice.
This weak give Eve a chance to cheat them. First, Eve can intercepts the public key from Alice for Bob and substitutes it with Eve's own public key to Bob. After Bob send back his public key , Eve will finally get a shared secret key paired with Bob.
Next, Eve will act as Bob and send her another public key to Alice. Then Eve can get a shared secret key paired with Alice.
That is, Eve can generate shared secret keys with them both
- SecretEve, that is same as the one Bob has: SecretBob
- Secret'Eve, that is same as the one Alice has: SecretAlice
Thus, Eve can build secure channels with them each other and act as a bridge to pass the messages between Alice and Bob. Alice still can talk to Bob through Eve, and vice versa. However, Eve can know anything that Bob talks to Alice, and all the Alice's messages to Bob by decrypting the received messages from Alice or Bob. Before re-encrypting with the appropriate key and transmitting them to the other party, Eve even can tamper the messages.
This is really dangerous. Using digital signatures is a possible solution to avoid this active attack, but it requires a public key infrastructure(PKI) to do the authentication.
One-way Function
The trapdoor function, or the one-way function, is the base of the network security today. Please read trapdoor function in appendix to get more detail.
Operation with More than Two Parties
The Diffie–Hellman protocol can work on more than two parties. Please read Diffie–Hellman in multiple parties in appendix to get more detail.