J-PAKE over TLS
In the case that there is no trusted third party like PKI in the network, the certificate of server/client can not be authenticated. That is, the communication parties can not verified each others, while they can still establish a confidential channel without authentication.
However, if there is a shared password between the communication parties, then we can use PAKE to authenticate each side. One approach is Secure modular password authentication for the web using channel bindings published on SSR 2014(We will use SSR2014 as this work later).
Here, we want to introduced a variant if SSR2014, named J-PAKE over TLS. The basic concept is same as SSR2014, but we add a little change.
Basic idea
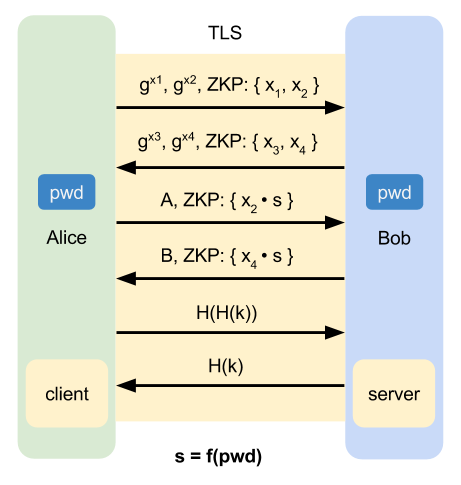 Establish the confidential TLS channel without authentication first,
and then authenticate both side by J-PAKE.
Establish the confidential TLS channel without authentication first,
and then authenticate both side by J-PAKE.
Man-in-the-middle
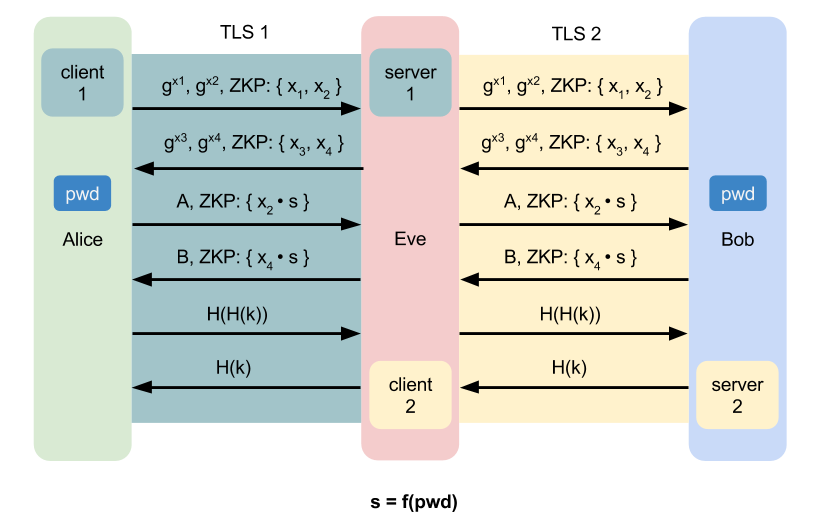 However, it can not prevent the man-in-the-middle(MITM) attack.
However, it can not prevent the man-in-the-middle(MITM) attack.
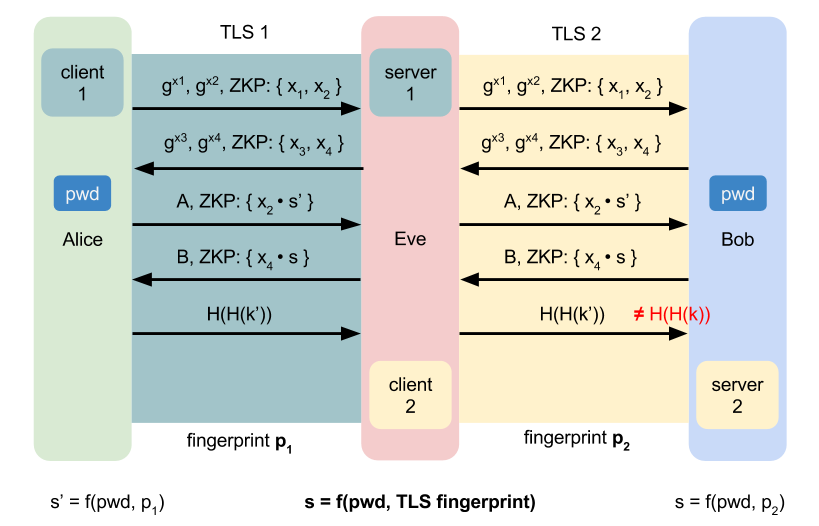
Mixing TLS fingerprint in the shared secret
To avoid MITM, we can mix the TLS's fingerprint in