J-PAKE Protocol
As a PAKE family member,
J-PAKE follows the general two-stage framework:
- Key Establishment Protocol:
Negotiate a one-time session key for the engaging parties.
- Key Confirmation Protocol:
Authenticate each other has the same session key.
The key confirmation part is easy to understand.
It's nothing different from the introduction of two-stage framework.
In this chapter, we will focus on the first stage to realize
the magic behind J-PAKE.
Before introducing, let we define the symbols first:
Let group G is a subgroup of Zp× with prime order q,
in which the discrete log problem is intractable
(Nevertheless, G also can be switched to Elliptic curve cryptography group).
Let g is the generator of G.
Typically, Schnorr group is used in this protocol.
The two communication parties, Alice and Bob,
both agree on group (G,g).
Let s is their low-entropy shared secret,
which can be a password or hash of a password,
and s≠0 is not empty.
The value of s is assumed in [1,q−1].
Key Establishment
The key establishment of J-PAKE executes in two rounds.
Round 1
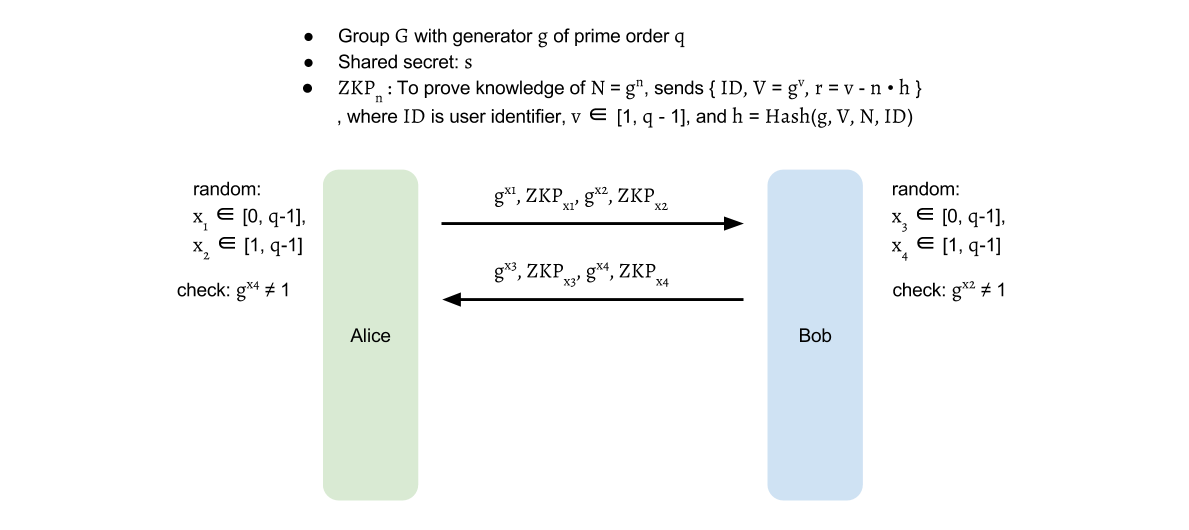
In round 1, Alice selects x1∈[0,q−1],x2∈[1,q−1]
then sends out gx1,gx2 with Zero-knowledge proof for x1,x2.
Similarly, Bob selects x3∈[0,q−1],x4∈[1,q−1] and
sends out gx3,gx4 with Zero-knowledge proof for x3,x4.
The above communication can be completed in one round
as neither party depends on the other.
When it finishes, Alice and Bob verify the received Zero-knowledge proof
and also check gx2,gx4≠1.
Round 2
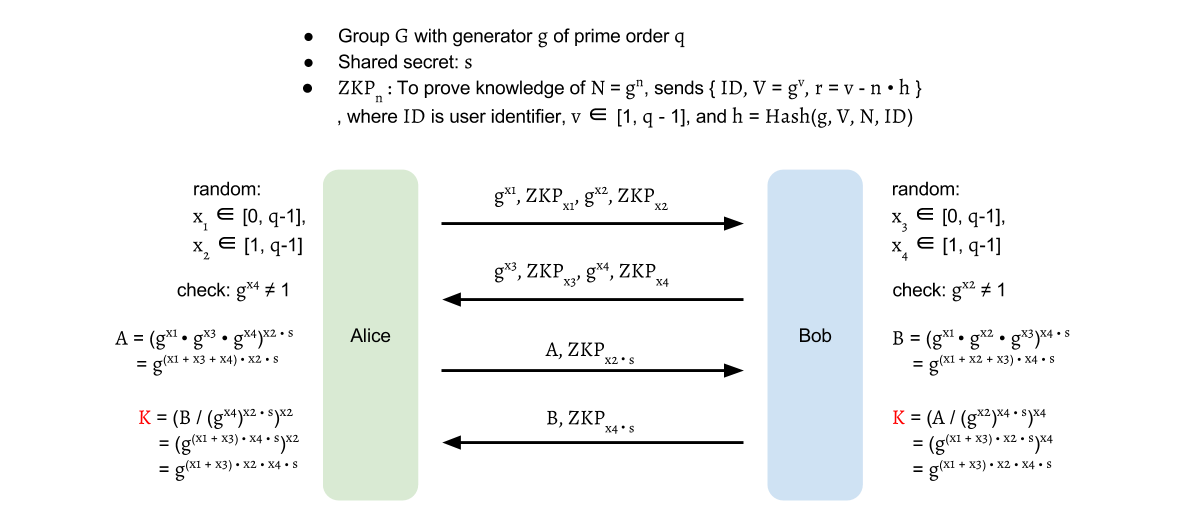
Alice sends out A=g(x1+x3+x4)⋅x2⋅s=(gx1⋅gx3⋅gx4)x2⋅s
and a Zero-knowledge proof for x2⋅s.
Similarly, Bob sends out B=g(x1+x2+x3)⋅x4⋅s=(gx1⋅gx2⋅gx3)x4⋅s
and a Zero-knowledge proof for x4⋅s.
After round 2, Alice computes K=(B/gx2⋅x4⋅s)x2=g(x1+x3)⋅x2⋅x4⋅s,
and Bob computes K=(A/gx2⋅x4⋅s)x4=g(x1+x3)⋅x2⋅x4⋅s.
With the same keying material K,
a session key can be derived for Alice and Bob: k=H(K),
where H is a Cryptographic hash function.
The division / here means multiplication with the inverse element.
For example, a/b=a⋅b−1=bq−1, where a,b∈G.
b−1 is an element such that b⋅b−1=1,
known as the inverse element of b.
From the fact that bq=1, where q is the order of G,
bq−i can be used as an inverse element of bi
because bi⋅bq−i=bq=1, where i∈N.
Therefore, the K can be computed by
KLIJAliceK , where q is the order of G=(gx2⋅x4⋅sB)x2=(B⋅g−(x2⋅x4⋅s))x2=(B⋅(gx2⋅x4)−s)x2=(B⋅(gx2⋅x4)q−s)x2=gx2⋅x4=(gx4)x2=L−s=Lq−s=B⋅I=(JAlice)x2
or
KLIJBobK , where q is the order of G=(gx2⋅x4⋅sA)x4=(A⋅g−(x2⋅x4⋅s))x4=(A⋅(gx2⋅x4)−s)x4=(A⋅(gx2⋅x4)q−s)x4=gx2⋅x4=(gx2)x4=L−s=Lq−s=A⋅I=(JBob)x4
Key Confirmation
There are several ways to achieve explicit key confirmation.
One simple method is to use hash-key
like SPEKE to do it:
Alice sends Bob H(H(k)), and then Bob replies with H(k).
Another method is use the session key k to
encrypt and decrypt a random value(random challenge)
like EKE.
Zero-Knowledge Proof
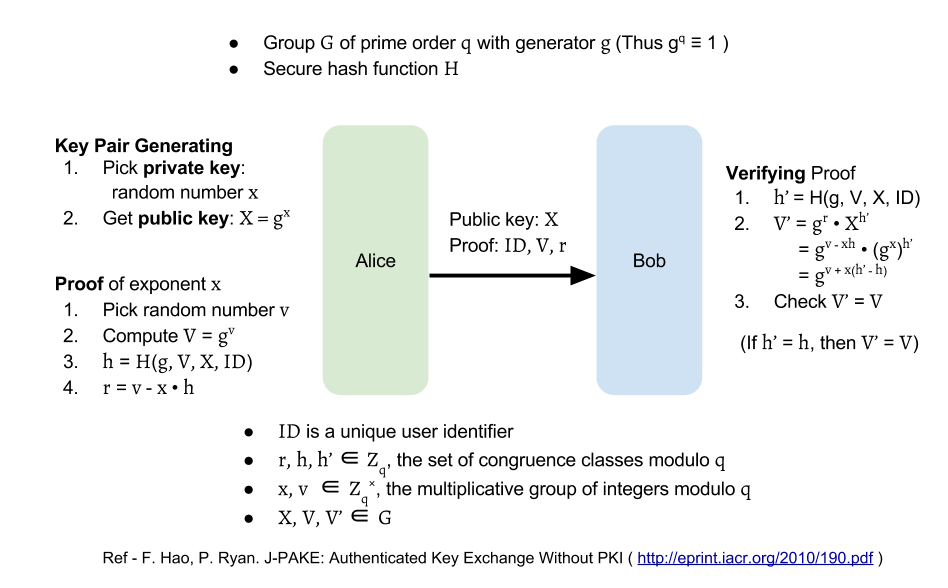 In the protocol, we need to produce a valid knowledge proof for the exponent.
As an example, we can use Schnorr signature mentioned in appendix to do it.
To prove the knowledge of the exponent for X=gx,
one sends out X with Zero-Knowledge proof: ID,V=gv,r=v−x⋅h,
where $ID$ is the unique user identifier,
v∈Zq and h=H(g,V,X,ID), H is a secure hash function.
The receiver then can compute their own h′=H(g,V,X,ID)
and verifies V=gr⋅Xh′.
The ID added here is to prevent Alice replaying Bob's signature back to Bob
and vise versa.
In the protocol, we need to produce a valid knowledge proof for the exponent.
As an example, we can use Schnorr signature mentioned in appendix to do it.
To prove the knowledge of the exponent for X=gx,
one sends out X with Zero-Knowledge proof: ID,V=gv,r=v−x⋅h,
where $ID$ is the unique user identifier,
v∈Zq and h=H(g,V,X,ID), H is a secure hash function.
The receiver then can compute their own h′=H(g,V,X,ID)
and verifies V=gr⋅Xh′.
The ID added here is to prevent Alice replaying Bob's signature back to Bob
and vise versa.
Why does J-PAKE need Zero-Knowledge Proof
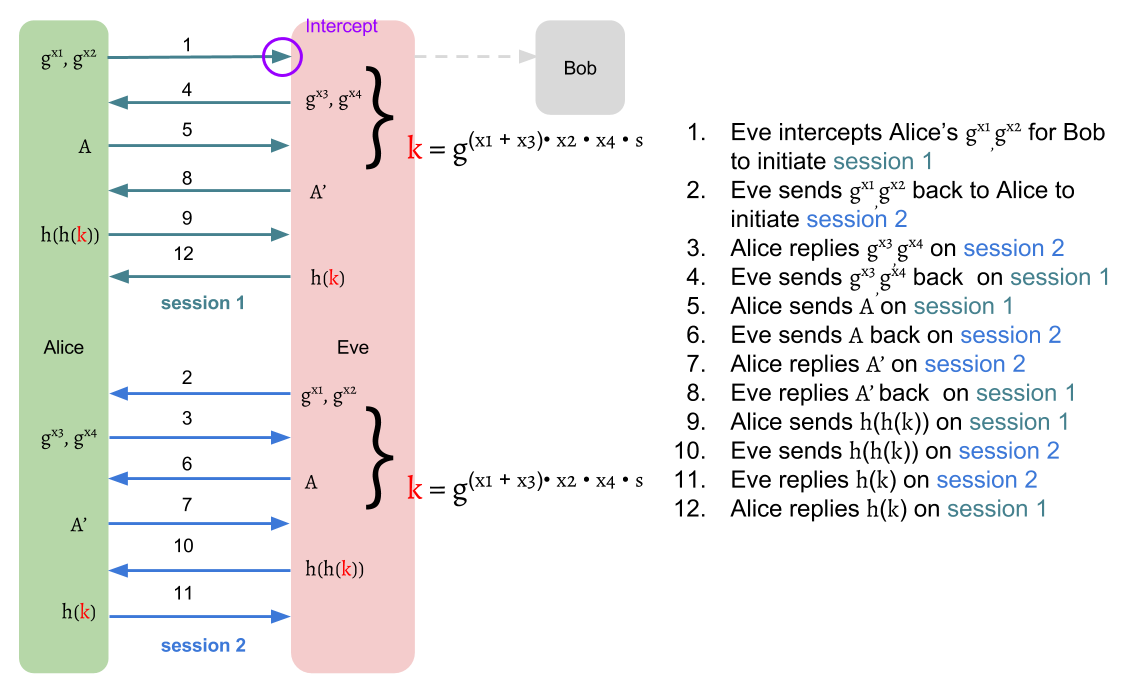 If we don't use ZKP here,
J-PAKE will suffer impersonation-attack like SPEKE
If we don't use ZKP here,
J-PAKE will suffer impersonation-attack like SPEKE
Can we use hash instead of ZKP
No. To use hash to verify, the two party must have the same secret.
If only one party has the secret, then the other has no way to verify it.
It doesn't has the value to hash, so it has no results to compare.
Why x2, x4 and s can NOT be 0?
K=g(x1+x3)⋅x2⋅x4⋅s
The attackers can intentionally choose x2=0 or x4=0
to force the K=1, even he doesn't know the password.
Therefore, the range of x2,x4 are specified in 1 to q−1.
This is also the same reason for s≠0.
Why don't we just select x1, x2, x3, x4 between 1 to q-1?
The K still can be 1 if x1+x3=0.
However, the probability is extremely low.
You can still select x1,x2,x3,x4∈[1,q−1]. It's valid.
But you will lose the combinations of
x1=0 paired to x2,x3,x4≠0
and x2=0 paired to x1,x3,x4≠0.
Examples
Let take the group in appendix for Group Theory as an example.
G={1,2,3,4,6,8,9,12,13,16,18} is a Schnorr group
with prime order q=11 and generator g=9,
which is the subgroup of Z23×={x∣0<x<23∩x∈N}.
Z23× is a multiplicative group of integers modulo p, p=23.
And let shared secret s=7(1≤s≤q−1).
Suppose Alice first chooses x1=9(0≤x1≤q−1),x2=3(1≤x2≤q−1)
and Bob chooses x3=5(0≤x3≤q−1),x4=6(1≤x4≤q−1),
the final results are as follows:
| Rnd |
Dir |
Alice |
Public |
Bob |
|
|
g = 9, q = 11, p = 23, s = 7 |
g = 9, q = 11, p = 23 |
g = 9, q = 11, p = 23, s = 7 |
|
|
x1 = 9, x2 = 3 |
|
x3 = 5, x4 = 6 |
| 1 |
→ |
gx1 = 2, gx2 = 16 |
gx1 = 2, gx2 = 16 |
gx1 = 2, gx2 = 16 |
| 1 |
← |
gx3 = 8, gx4 = 3 |
gx3 = 8, gx4 = 3 |
gx3 = 8, gx4 = 3 |
| 2 |
→ |
A = 12 |
A = 12 |
A = 12 |
| 2 |
← |
B = 18 |
B = 18 |
B = 18 |
|
|
K = 11 |
|
K = 11 |
gx1,gx2,gx3,gx4 can be directly get from
example Schnorr group in appendix.
Next, we will use gx1,gx2,gx3,gx4
to compute A,B,K.
You can try all the following computation process
on Online Big Number Calculator to verify the results.
A≡(gx1⋅gx3⋅gx4)x2⋅s(modp)≡(2⋅8⋅3)3⋅7(mod23)≡(48)3⋅7(mod23)≡23⋅7(mod23)≡(23)7(mod23)≡87(mod23)≡12
B≡(gx1⋅gx2⋅gx3)x4⋅s(modp)≡(2⋅16⋅8)6⋅7(mod23)≡(256)6⋅7(mod23)≡36⋅7(mod23)≡(36)7(mod23)≡167(mod23)≡18
To compute K for Alice, we first start with (gx4)x2
to get gx2⋅x4.
Next, we can use (gx2⋅x4)−s=(gx2⋅x4)q−s
to get g−(x2⋅x4⋅s).
Then, JAlice=gx2⋅x4⋅sB can be calculated
by JAlice=B⋅g−(x2⋅x4⋅s)=B⋅(gx2⋅x4)−s
Finally, K=(JAlice)x2.
LIJAliceK≡(gx4)x2(modp)≡33(mod23)≡4≡L−s≡Lq−s(modp)≡411−7≡44(mod23)≡3≡B⋅I(modp)≡18⋅3(mod23)≡8≡(JAlice)x2(modp)≡83(mod23)≡6
In the same way, Bob can start with (gx2)x4
to get gx2⋅x4.
Then apply (gx2⋅x4)−s=(gx2⋅x4)q−s
to K=(gx2⋅x4⋅sA)x4=(A⋅(gx2⋅x4)−s))x4.
LIJBobK≡(gx2)x4(modp)≡166(mod23)≡4≡L−s≡Lq−s(modp)≡411−7≡44(mod23)≡3≡A⋅I(modp)≡12⋅3(mod23)≡13≡(JAlice)x4(modp)≡136(mod23)≡6
References


 In the protocol, we need to produce a valid knowledge proof for the exponent.
As an example, we can use Schnorr signature mentioned in appendix to do it.
To prove the knowledge of the exponent for ,
one sends out with Zero-Knowledge proof: ,
where $ID$ is the unique user identifier,
and , is a secure hash function.
The receiver then can compute their own
and verifies .
The added here is to prevent Alice replaying Bob's signature back to Bob
and vise versa.
In the protocol, we need to produce a valid knowledge proof for the exponent.
As an example, we can use Schnorr signature mentioned in appendix to do it.
To prove the knowledge of the exponent for ,
one sends out with Zero-Knowledge proof: ,
where $ID$ is the unique user identifier,
and , is a secure hash function.
The receiver then can compute their own
and verifies .
The added here is to prevent Alice replaying Bob's signature back to Bob
and vise versa. If we don't use ZKP here,
J-PAKE will suffer impersonation-attack like SPEKE
If we don't use ZKP here,
J-PAKE will suffer impersonation-attack like SPEKE